Update: 07/15 7 As reported by Kafeine, Magnitude EK is now using this zero-day.
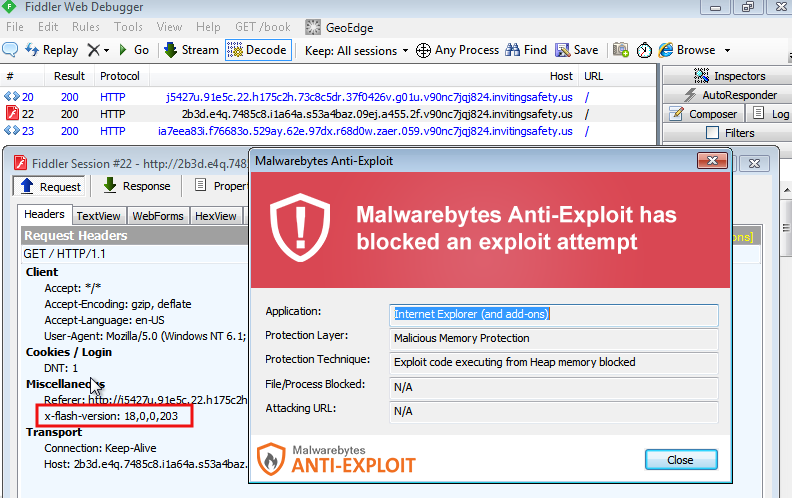
Update: 07/14 7 As reported by brooks_li, RIG EK is now using this zero-day.
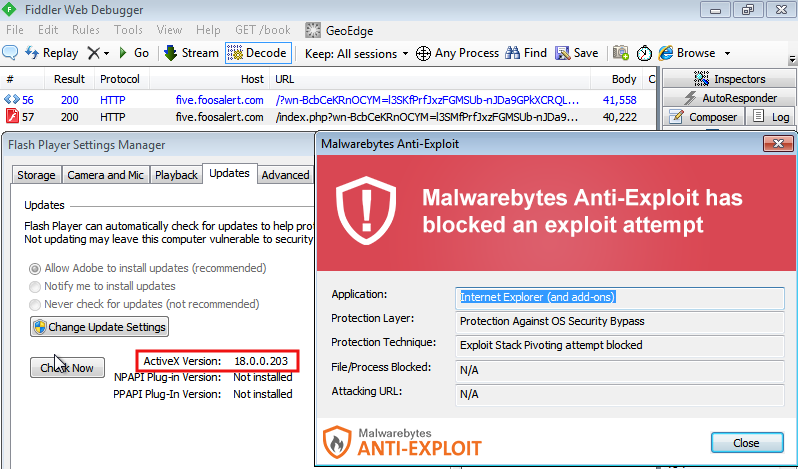
Update: 07/13 7 AM PT As reported by Kafeine, Neutrino EK is now using this zero-day.
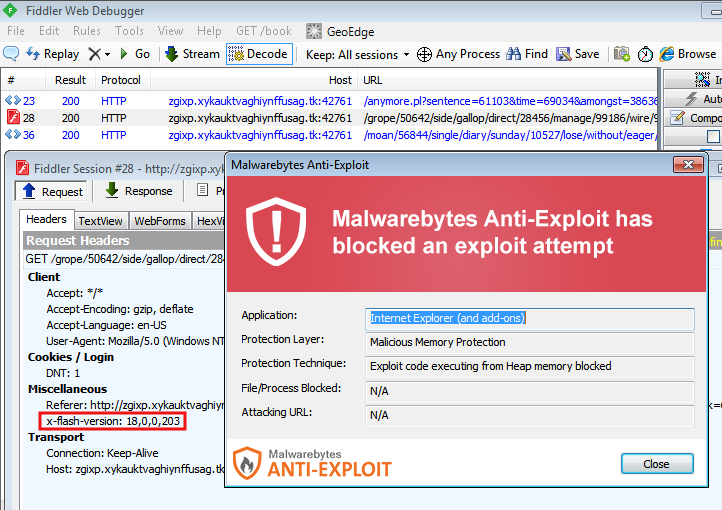
Update: 07/11 9 AM PT As reported by Kafeine, Angler EK is now using this zero-day.
Malwarebytes Anti-Exploit blocks this attack:
– – – –
The Hacking Team debacle has made headlines all week long and sparked a lot of debates over the sale of cyber weapons to various governments, including oppressive regimes.
It didn’t take very long for someone to identify a zero-day vulnerability in the Flash Player within the leaked documents. That vulnerability was almost instantly weaponized in exploit kits affecting consumers and businesses alike.
On a late Friday night, yet another zero-day targeting once again the Flash Player has been uncovered from this very same Hacking Team archive. Adobe released a security bulletin shortly after:
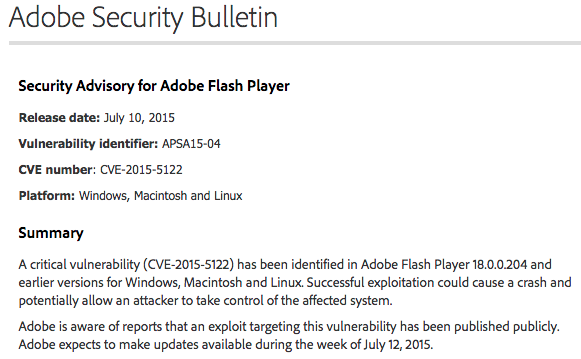
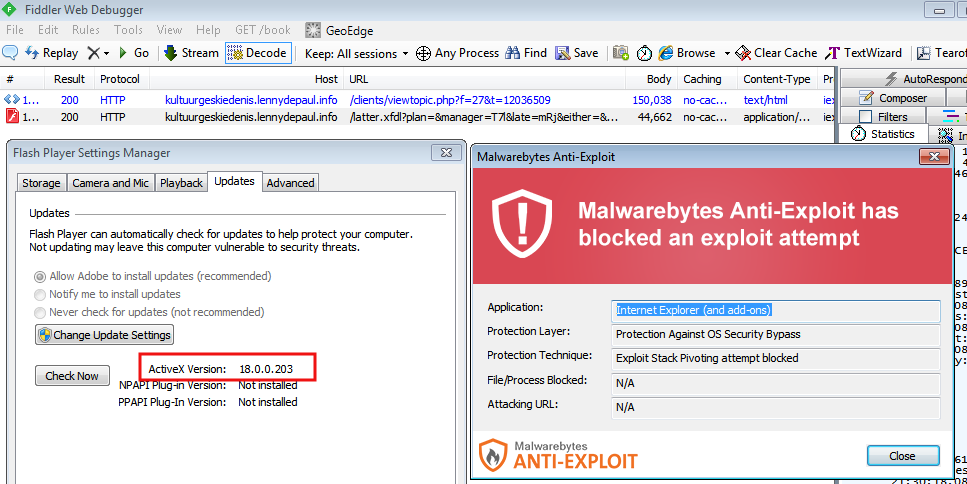
Malwarebytes Anti-Exploit users are already protected against this specific attack (CVE-2015-5122):
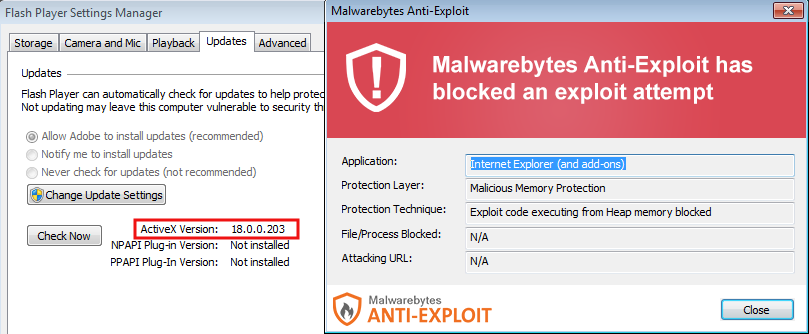
While the software vendor quickly works on a patch expected to be released the week of July 12th, cyber-criminals are without a doubt racing against time to get it into their exploit kit.
During that period of time when no patch exists and the vulnerability is exploited, the number of potential victims of drive-by download attacks is considerably higher.










