We identified one of the largest malvertising campaigns in recent months going through 10 different ad domains receiving massive volumes of Internet traffic.
Although we only recently uncovered and reported this campaign, telemetry data indicates that it actually started on October 21, making this at least a three-week operation.
This malvertising attack preyed on visitors to sketchy websites offering anything from torrents of copyrighted movies, live streams of the latest flicks, or pirated software.
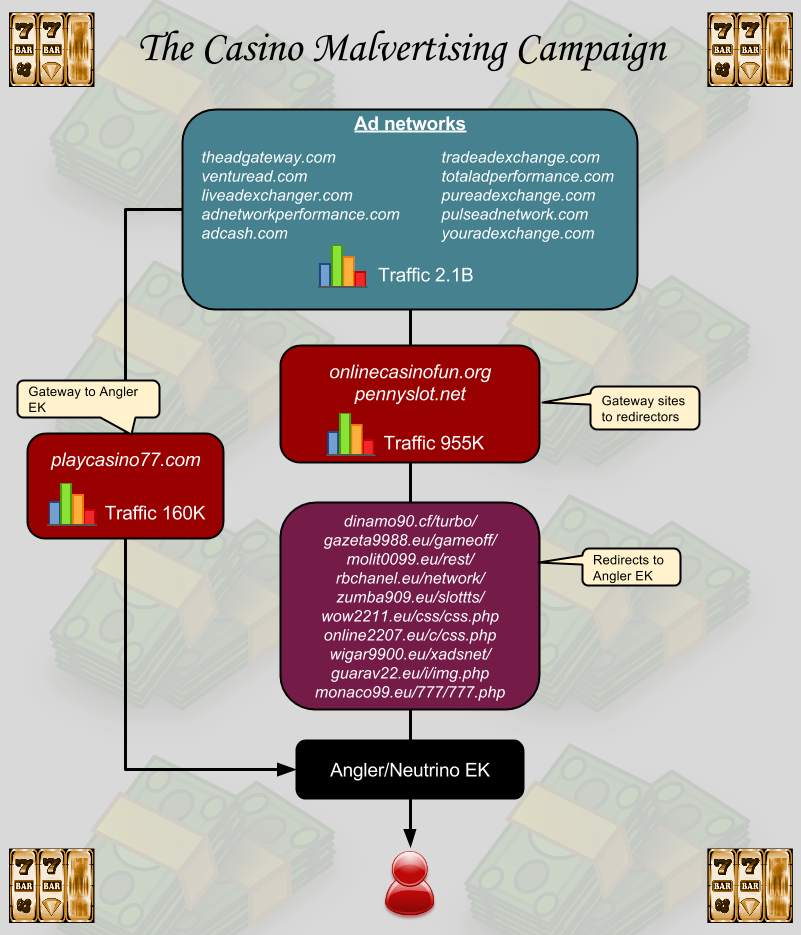
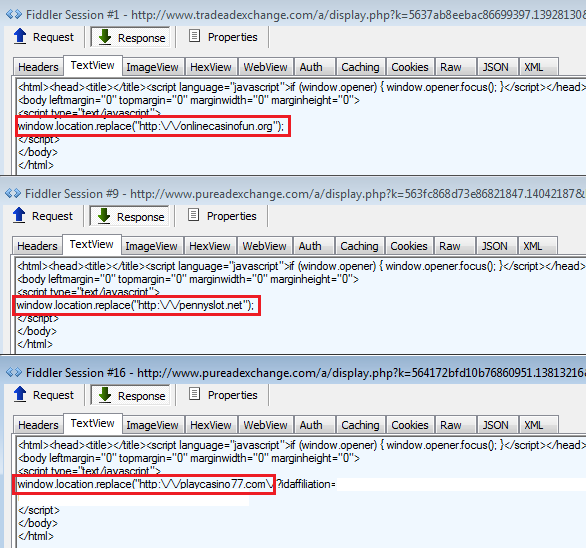
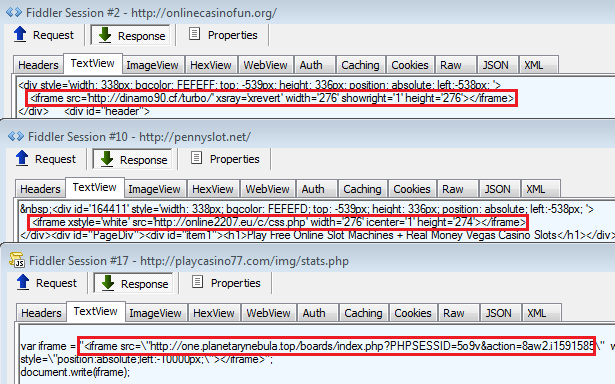
The malicious ads would automatically (no click required) redirect users to a casino website used as decoy to silently load malicious iframes from disposable domains which ultimately lead to the Angler exploit kit. In one case, the casino website was a direct gateway to Angler EK.
(Update: As of Nov. 17 we noticed Neutrino EK was also pushed)
Since this campaign affected dubious publishers likely to turn a blind eye on ‘advertising issues’ as well as visitors knowing they were consuming illegal content, there was little reason for anybody to report any incident. In fact, each of these malvertising attacks taken on its own does not stand out, but realizing that they were all connected gives us the bigger picture in how large of an operation this was.
The ad networks were almost all registered via Domains By Proxy LLC, meaning no information was available about the registrant but they were all through GoDaddy and on the same ASN: AS15169. This made us believe that they were actually all related to one another. Moreover, one of them, AdCash, did have a point of contact and this is how we were able to report the incidents.
A look at some of the stats behind those ad domains shows some staggering numbers. According to SimilarWeb a service that estimates website traffic and provides various analytics, these ad networks generated over 2 billion visits in October.
To be clear, this is not how many people were exposed to malvertising since this only affected a few particular rogue campaigns, and not all campaigns running on these networks.
However, we can get a better idea of how many people may have been redirected to Angler EK if we look at the stats of the casino sites that acted as an intermediary for the exploit kit. Interestingly, before September, the traffic on those three domains was quasi nonexistent but all of the sudden spiked through the roof for a combined total of over 1 million visits.
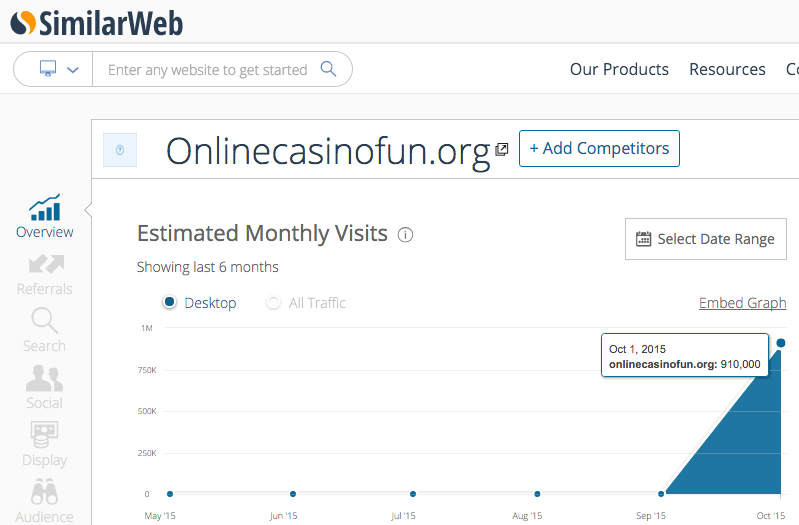
Analytics provided by SimilarWeb
In all likelihood, a very large number of people were exposed to malware because of this campaign. Over the three-week course, several different payloads were dropped by Angler EK.
We found the infamous CryptoWall ransomware as well as the Bunitu Trojan. A list of malware hashes is available and can be found within the technical section below.
We contacted AdCash on November 10th and the following day the malvertising attacks appeared to have stopped. However, on November 14th we observed another incident again also using one of the casino websites but with a .space domain now to redirect to Angler EK.
Ad call: adcash.com/script/packcpm.php?k=56476941be81d7081580.15104969{redacted} Compromised casino site: pennyslot.org/ Redirector: 1depen.space/888/roll.php Angler EK: qwertymerty16.space/forums/index.php?PHPSESSID=ehzik&{redacted}
We will continue to monitor and report future incidents we encounter via this ad network and take necessary actions to protect our users from malware. Malwarebytes Anti-Exploit detects and protects against Angler exploit kit.
Highlights:
- Torrent, crack, video sites targeted
- Malvertising via AdCash and related networks (> 2 billion traffic)
- Casino websites used a decoy/redirectors ( > 1 million traffic)
- Angler / Neutrino exploit kits
- Over 30 different malware payloads
- Three-week campaign
Technical details
Ad networks:
- theadgateway.com
- tradeadexchange.com
- venturead.com
- totaladperformance.com
- liveadexchanger.com
- pureadexchange.com
- adnetworkperformance.com
- pulseadnetwork.com
- adcash.com
- youradexchange.com
Casino websites:
- onlinecasinofun.org
- pennyslot.net
- playcasino77.com
Redirectors:
- dinamo90.cf/turbo/
- gazeta9988.eu/gameoff/
- molit0099.eu/rest/
- rbchanel.eu/network/
- zumba909.eu/slottts/
- wow2211.eu/css/css.php
- online2207.eu/c/css.php
- wigar9900.eu/xadsnet/
- guarav22.eu/i/img.php
- monaco99.eu/777/777.php
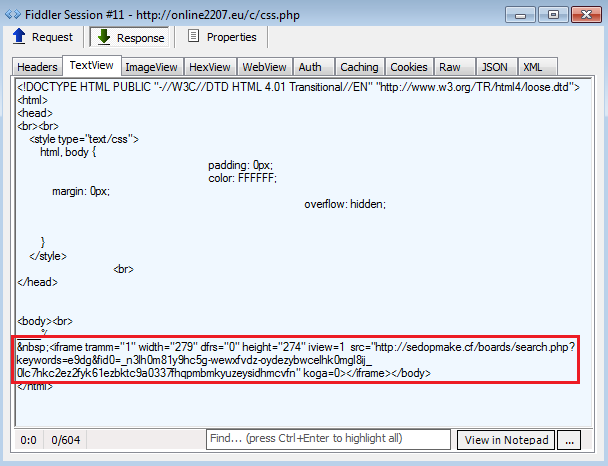
Traffic sequence overview:
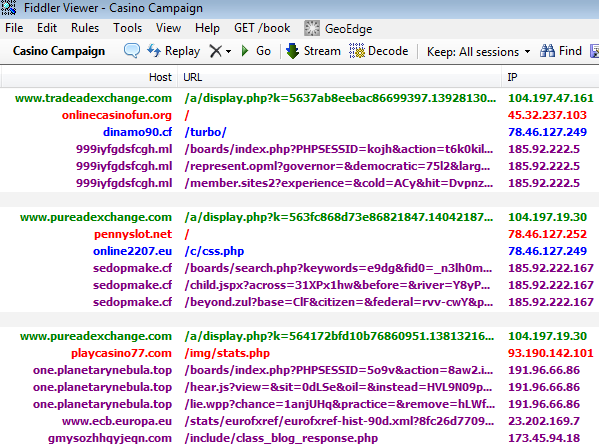
Update (Nov 17): Neutrino EK also pushed
Malware hashes:
A list of samples we collected over the three-week campaign can be found here.










